Over the last week there’s been a surprising amount of concerned speculation that President Biden would be unable to take his apparently beloved Peloton Bike to the White House, citing security concerns. The reason is that the Peloton Bikes contain not only a network connection, but also a camera and a microphone. The camera and microphone are intended to be able to do a workout with a friend, akin to Facetime or such, though in reality very few people tend to use them. There’s also Bluetooth and WiFi.
Still – cameras and microphones, as well as both wired and wireless connections can indeed pose security concerns in any technology device, be it a bike or a phone. It’s why in most high-security environments, such devices are tightly controlled (if allowed at all). However, the amount of speculation that somehow this would stop the Biden’s from bringing their Peloton bike is silly.
Here, let me explain.
(Preemptive warning: Politically focused comments – on either side of the aisle – will be immediately deleted. There are plenty of other places in the world to drop those, I’m here for the tech – so let’s focus on that.)
Peloton Bike Tech:
Now the first thing to know about the Peloton Bike is that there are actually two main models of the Peloton Bike: The Bike, and the newer Bike+. They are similar in many ways, but also quite different. From an underlying bike frame standpoint (the big bulky metal part), they’re actually identical. However, the differences are in the screen, as well as on the Bike+ there is an electronic resistance unit. But that doesn’t matter in this conversation.
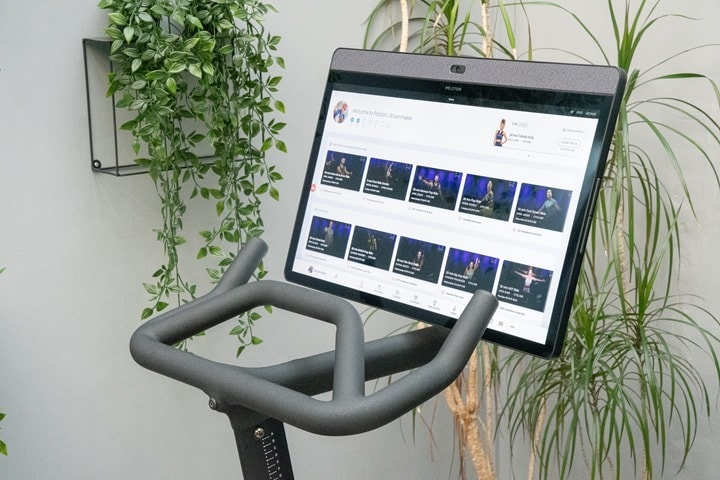
The basic design of both bikes is that the screen up top is the everything from a smarts standpoint. It’s essentially a giant Android phone, using a large touchscreen instead. The unit runs Android (different versions depending on the bike), but the average consumer would never really notice that. However, that Android platform does make it far more appealing (and easy) for attackers (or hobbyists) to tweak with.
Both bikes have cameras in them at the top of the screen, however, the Peloton Bike+ also has a camera cover. This small piece of plastic allows you to cover the camera.
Both bikes have mics in them, also at the top of the screen. In the case of the original Bike it’s actually visible just above the camera on the bezel of the screen. Whereas the Bike+ appears to have it behind the speaker fabric.
Both Peloton Bikes have dedicated headphone jacks as well.
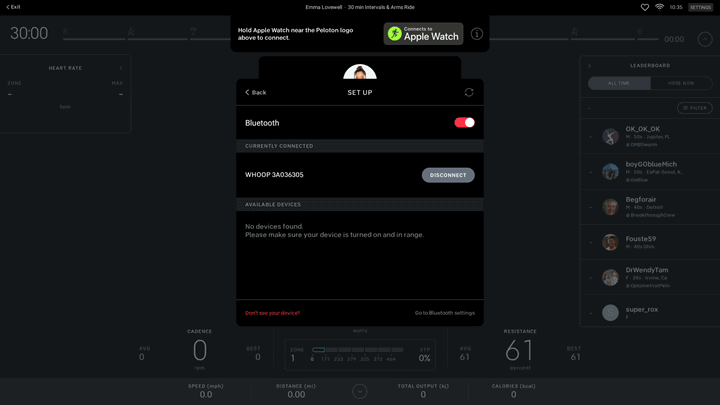
When it comes to connectivity, both bikes have WiFi connectivity, though only the original Bike has wired ethernet built-in. Instead, the Bike+ would require someone purchase a USB-C to Ethernet dongle in order for wired connectivity. There’s also Bluetooth audio devices (and heart rate sensor pairing). If looking at the device holistically from a security standpoint, it’s likely they would aim to physically disable the Bluetooth connectivity as well, as that could be paired to nearby Bluetooth audio devices otherwise.
Neither the camera nor microphone are required for day to day usage, however network connectivity is. Without network connectivity you can’t load the classes to take (or take live ones), nor can you see any of your training data over time. You can however use the bike without connectivity in a base mode without classes (basically just as a simple spin bike).
Now while all of these things are considered security risks, they’re hardly without precedent in the White House. In fact ultimately, the Peloton bike as noted earlier is just a giant Android phone. But various US government agencies literally have divisions that are focused on taking apart devices and making them more hardened. But one has to first decide what type of ‘space’ they’re going into. For example, while there are many portions of the White House that are considered a sensitive compartmented information facility (SCIF) where classified information can be discussed – there are plenty of portions that are not. It’s in these portions that most day to day work happens, and where staffers carry both government-issued and personal devices (the exact policies on this have varied from administration to administration, and even within an administration).
Sure, one should always be careful with any device and discussing both official and classified information. But iPhone, Android phones, smart watches and such are the norm these days. And for classified information that’d be discussed in a classified ‘facility’ (the term facility here is more of a construct than a specific building – in some locations the facility can be the entire building, and in others just a single tiny room).
Still, governments around the world have a long history of securing devices, both in unclass (unclassified) and high side (classified) areas. For high-security situations, they’ll dismantle them, understand how they work, remove risky components, and put them back together again. This is hardly news. One only needs to look at the current PDB (Presidential Daily Brief) being delivered on an iPad to see that, as a public example.
While it’s rumored that former First Lady Michelle Obama has, or had, a Peloton Bike delivered without a camera/mic, that would do little to assuage security divisions about putting any connected device within the White House residence. If the location of the device warranted, those same divisions would still take apart the device and do their normal security work. The removal of a camera/mic by Peloton would merely save government teams time in making the device work properly after disabling those components (as it would usually fail various internal checks).
No matter which flavor of bike shows up, White House staffers within EOP would then work to follow standard security guidelines (so-called STIG’s) published by NIST for Android devices, then in conjunction with other intelligence agencies they’d complete a more detailed assessment of the risks of that specific Peloton model to decide where it might be placed, and what hardening steps may or may not be taken. Given how many government officials (such as embassy staff and past executive officials) have Peloton bikes, this has undoubtedly been done many times before and well documented.
Finally, while my Peloton Bike is currently sitting in our bedroom – a place where, in a White House setting, classified information would undoubtedly be discussed as any president mulls through tough decisions, there’s zero need for the bike to sit there in the White House. After all, the White House is a vast building including a gym, bowling alley, and theater. A Peloton Bike could easily be placed in the White House gym or another secured room that is only used for working out. You can see some images of the long lineup of fitness machines in some White House gym photos here.
Thus ultimately, the task of securing electronic/connected devices to work in the White House is something that is a well-understood path that’s been done countless times before on far more technically challenging devices. And more importantly, it’s something done on a continual basis for far more mundane devices. Sticking a connected bike in a storage room somewhere is pretty low on the complexity factor for those divisions.
Thus, I’ve got no doubts that both the President and First Lady will continue using their bike, whichever model it is, for some time to come.
With that – thanks for reading!
(And again – preemptive warning: Politically focused comments – on either side of the aisle – will be immediately deleted. There are plenty of other places in the world to drop those, I’m here for the tech – so let’s focus on that.)
Found This Post Useful? Support The Site!
Hopefully you found this review/post useful. At the end of the day, I’m an athlete just like you looking for the most detail possible on a new purchase – so my review is written from the standpoint of how I used the device. The reviews generally take a lot of hours to put together, so it’s a fair bit of work (and labor of love). As you probably noticed by looking below, I also take time to answer all the questions posted in the comments – and there’s quite a bit of detail in there as well.
If you're shopping for the Peloton Bike+ or any other accessory items, please consider using the affiliate links below! As an Amazon Associate I earn from qualifying purchases. It doesn’t cost you anything extra, but your purchases help support this website a lot.
Here's a few other variants or sibling products that are worth considering:
I've also put together a quick list of some of my favorite or most compatible accessories for this unit:
And of course – you can always sign-up to be a DCR Supporter! That gets you an ad-free DCR, access to the DCR Shed Talkin' video series packed with behind the scenes tidbits...and it also makes you awesome. And being awesome is what it’s all about!
Thanks for reading! And as always, feel free to post comments or questions in the comments section below, I’ll be happy to try and answer them as quickly as possible. And lastly, if you felt this review was useful – I always appreciate feedback in the comments below. Thanks!







































First paragraph you wrote: “President Biden would be unable to take his apparently beloved Peloton Bike to the White, ” – I think you meant “White House”
Weird, thanks!
“Sure, one always be careful with any device…”
Maybe ‘one SHOULD always be careful’?
While I am sure that there are a bunch of things that can be done to harden a Peloton or other connected fitness device, I am not as much concerned with what the White House IT staff will do to the Peloton bike, as I am with the President’s health data on Peloton.com. If someone were to hack Peloton (the weakest link in this case), it would have access to things like – the President’s HR data, and the times of day he works out (assuming he has a relatively routine schedule when he is in Washington). Leaking the HR data could allow people to speculate on his health (or if he misses workouts for a couple of weeks in a row, with no ostensible reason).
For that token, I’d probably be equally concerned about connected fitness watches as wel.
Which leads me to this question – are connected fitness apps required to be HIPPA compliant?
Health data is small potatoes. It could be an indication of something or another, but the Big Intelligence Coup other countries are looking for wouldn’t come from that.
Well funded adversaries can do amazing things if they think the payoff can be worth it. Think Stuxnet destroying uranium enrichment hardware. It may not be likely, but it is certainly not outside the realm of possibility that a certain bike meant for a certain prominent politician had a specific modification done to the breadboards that adds additional ‘features’ such as a piezoelectric mic disguised as a capacitor with associated hardware to store and transmit recordings on detection of an internet connection. Purely my imagination, and I am not very imaginative. Likely? No. Possible? Yes, especially considering where the production is probably taking place.
Ray’s article is a good primer on the topic, but just realize that he is barely scratching the surface of IT security in a classified environment.
Agree, the workout HR details of a person – even the president, wouldn’t really be super valuable. HRV details would be more valuable, but best we all know, Peloton isn’t recording that data.
“but it is certainly not outside the realm of possibility that a certain bike meant for a certain prominent politician had a specific modification done to the breadboards that adds additional ‘features’ such as a piezoelectric mic disguised as a capacitor with associated hardware to store and transmit recordings on detection of an internet connection.”
Indeed, in fact, it would be a good reason to *NOT* take a custom build Peloton, versus picking an off the shelf unit that’s less likely to be tampered with on scale than a custom build one that’s more vulnerable to people in that entire chain of awareness.
“Ray’s article is a good primer on the topic, but just realize that he is barely scratching the surface of IT security in a classified environment.”
Yup, I aimed to keep it pretty basic here. The depths of what’s required to install equipment into a classified environment is incredibly long (heck, even unclass), but ultimately, I don’t think they’d go the class route. They’re just gonna stick it somewhere else in the White House that’s a low risk area for such sensitive discussions. Which, is ultimately all part of a full scope threat assessment.
Place bike in a dedicated ‘gym’ room with its own dedicated network (wired or wireless access point). Security staff only enables gym network when bike is in use and if anything “presidential” needs to interrupt his workout they turn off the network.
I can’t imagine a feature I’d want LESS than a camera and mic while I’m working out and sweating my butt off! Especially all close up like that, and at the least flattering angle known to man. LOL. Does anyone actually use this feature?
I actually thought that too until the pandemic. Now I ride a regular schedule with various friends using video chat. It’s a safe way to connect, workout together and motivate one another. No different than huffing and puffing together at the gym. I was super skeptical but I love it now!
I think you’d be surprised. I’ve done group rides on Zwift where we video chat at the same time – sometimes it’s a nice little boost of motivation to see everyone else spinning away and sweating it out with you!
really cool post – Thanks for the insights.
The former president had an internet connected golf simulator installed in the White House. They’ll manage a bike as well.
link to time.com
Thanks for the detailed post. It seems kind of crazy this even needs to be a story, though. The White House staff should be more than capable of installing this kind of equipment securely.
I’m highly disappointed there aren’t pinball machines in the White House game room.
Clearly they’ll put a peloton bike in there if they want. The point of the story wasn’t really to worry about whether they could or could not, it was to send a signal to people that Joe has and uses a peloton. The story was placed in the media for that reason alone. This isn’t a political thing by me, all presidents will do those types of things (they release the books they supposedly read, music lists they supposedly curate, that they have a golf simulator set up, etc).
Nothing more, nothing less.
Easy fix.. ditch that POS and get a Neo LOL
i second that !
Ironically, it wouldn’t really solve the problem. For example – if he went on Zwift, he’d still have a connected internet device. It’d just just from being a giant Android phone to being an iPad/iPhone/Android/Mac/PC – but the problem is still basically the same.
Sure, there are more disconnected/offline options in the app world, but all of those do require at a minimum Bluetooth/ANT+ remaining enabled.
Zwifting with POTUS would be awesome though. Imagine the size of that group ride! Speculation about peak Zwift next January if he switches over?
I once worked with an agency who needed an air gapped system, so any info coming in had to be printed or transcribed and manually entered to the next system. This was labour intensive and required people – we don’t trust people – so a long conversation ensued about scanners, then MFDs, then fax, and finally instead of fax we could use a modem!
It was very entertaining :)
I wonder if a gps watch like garmin would be hardened. I. That data that shows a presidents location etc would be a security issue I know it not real time (except for live tracking) but could someone use it that way?
President Obama had a Fitbit Surge, which was Fitbit’s GPS activity tracker.
One could use it (or Garmin), largely offline without any real issues. Generally speaking, Garmin is really the only option left where no online account/connection is required at all if you don’t want it. All other devices on the market require at least an initial instantiation with a phone/online platform.
President Dmitry Medvedev in Russia used to wore Garmin – first Quatix 3, then switched to 935.
Presumably President Biden could always substitute secure spin classes with actual people in the room. Get the secret service on spin bikes plus an instructor and peppy music. Tada! No security issues. But yes, it also seems pretty trivial to neutralize the camera and microphone
But then you have to neutralize people that know too much. Like a spin class instructor that knows that you gave up after 4.5 minutes in a 5-minute interval…
Did you ever post the peloton reviews? Interested to hear more on the bike+ accuracy.
Haven’t quite finished it yet. But, the Bike+ accuracy continues to be crazy good for me.
So, if President Biden were to Zwift, would his avatar have to be accompanied by a virtual Secret Service detail?
Hi Ray, interesting post – any progress with the full Peloton/Peloton + review?
Yeah, I just need to wrap that up and get it out. Or, roughly where I was months ago – which is ironic because I’ve got boatloads of data (including another set of rides today). Sigh.
Two lines stand out
“cameras and microphones, as well as both wired and wireless connections can indeed pose security concerns in any technology device”
“while my Peloton Bike is currently sitting in our bedroom”
Hmmmm!
Fear not…it’s facing the wall. :)
For a consumer, I put this in the pretty low risk category, mainly because the threat avenues are pretty low here:
A) Option 1: Break into Peloton’s system, then gain downstream control of a Peloton bike at the admin rights level via pushing software updates or such that give more control. Technically possible – absolutely. Easy to pull off? Not really. And most importantly: Not worth it for me specifically (but of course undoubtedly very worth it for other celebs).
B) Option 2: Break into my WiFi network, then from there break into the Peloton bike itself, and finally, do what one wants to do. The barrier for entry is high here, and would require being within range of my home.
C) Option 3: This is a variant of Option 2 where you find a vulnerability in the Peloton bike-side platform or Android OS that allows a non-Peloton actor to access the bike without direct access to the network.
Like anything in security, there’s more options than these – but these are the quickest atop my head.
So you’re not going to cough up for that tape then ……… :)
Haha…stay tuned! We discussed it in tonight’s recording of the DCR Quarantine Corner. Should be out in the morning, The Girl already finished editing it. I just need to render/upload/e-mail.
Mics and cameras are largely useless to an attacker without a means to exfil that intel. I wonder, if he is able to use the bike online, how that connectivity will be provided and secured. I suspect there are many unclass internet connections into the White House, or connections that end at the White House but originate from elsewhere and break out either using a standard overt ‘DoD’ connection, or via some sort of un-attributable connection… I would be amazed if you couldn’t surf the web in the WH, with your traffic appearing to originate from x or y country.
2 further things with that – attribution of that traffic and ‘stained’ exfil from the bike that may therefore give away the traffic and its origin, and getting anything useful out over that connection without some sort of traffic/malware/spyware capabilities picking it up.
All that assumes you’ve got an implant on the bike able to collect something useful, or malware’s ability to bridge to other networked kit and act as a command/control point and collect intel from elsewhere in the network.
All very possible, in theory!…. but suppose we’ll never know.
Generally speaking most government organizations that work with low side and high side data will have two computers at a persons desk:
1) Computer on the classified network
2) Computer on the unclass network
Where the unclass network leads from an internet standpoint varies by organization. For less concerned organizations, it’ll actually be identifiable as part of the IP and domain provided that I can even see in my analytics data here – clearly identifying the US Government organization name the person is browsing from.
In some cases, where an organization might want that hidden, it’ll plop out into various general external points that could look like anything from a fake organization to a real but not correct organization, to almost no identifier at all. The higher up the ladder you go in wanting to cover these tracks, the more effort you put into how disposable this is, and how often a given endpoint is used. Finally, who an organization is trying to hide from generally matters more. If you’re trying to hide employees at the White House showing up on DCR’s analytics reports, that’s easy enough. Whereas if you’re trying to hide an attack from a state, more effort is given there. Most things sit somewhere in the middle.
I am glad he is interested in keeping himself fit. I know a lot of presidents have played golf, but that really is not much of a workout, especially if they use a cart. Keep cranking out the miles, Mr. President!
Golf is a pretty good workout if you walk the course carrying your bag.
18 holes is a 5-6 mile walk, generally with hills, with 15 pounds on your back. Go do it in 85 degree F sun and report back.
concerns of the peloton are overblown. as ray suggests, put it in an unsecured area of the WH…then connect to a separate unclassified network of which i’m sure there are options available in the WH, then have one of the secret-service folks create a bogus account for Biden to use, and lastly put a piece of tape over the camera…VOILA!
TOP dog Ray!! Many thanks for this article. Will you do Trump’s Peleton bike too…??
The White House is huge, Joe Biden should just use a normal bike and cycle all over the place. Good exercise and a lot of fun!
Slashdot has updated information pertaining to this post.
link to it.slashdot.org
Yeah, I don’t really see it as an impact though in this scenario. Practically speaking, this bug basically just allowed the standard-issue profile data for accounts marked private, rather than being blocked.
While that’s undoubtedly concerning, in the grand scheme of data leaks – it’s not that huge, especially considering none of the data is tied to actual location, or real names. It basically just listed what is normally found on a Peloton public profile.