
A German IT security firm has published a list of 8 different security bugs found in all COROS watches that give essentially full access to not only the user’s watch, but also their COROS account. This includes everything from interrupting a workout (during the workout), to resetting the device remotely, as well as accessing/downloading all your COROS.com data.
The list of security issues was originally listed to be for just the COROS Pace 3 watch; however, I have confirmed with COROS that it actually impacts all COROS devices, as all COROS watches (+ bike computer) utilize the same Bluetooth connectivity code between the watch and phone, where the issue lies.
The company outlined the issues in their post, which consolidates it down to six core gaps (as part of 8 specific security bugs):
– Hijacking the vicitim’s COROS account and accessing all data
– Eavesdropping sensitive data, e.g. notifications
– Manipulating the device configuration
– Factory resetting the device
– Crashing the device
– Interrupting a running activity and forcing the recorded data to be lost
The IT security firm researcher, Moritz Abrell, had initially discovered the vulnerabilities on March 10th, 2025, and notified COROS on March 14th, 2025. COROS immediately confirmed receipt of the issue on March 14th, 2025 as well. However, after that COROS went silent for another month, before finally responding back on April 15th, 2025 that it would fix the issues by the end of the year.
Disclosure Timeline (as outlined in Advisory):
2025-03-10: Vulnerability discovered
2025-03-14: Vulnerability reported to manufacturer
2025-03-14: Confirmation of receipt received
2025-03-17: Asked the manufacturer for an update
2025-03-31: More information provided to the manufacturer
2025-04-07: Asked the manufacturer for an update
2025-04-14: Informed the manufacturer about the assigned CVE-ID and asked for an update once again
2025-04-15: Answer received from the manufacturer; manufacturer informed SySS GmbH that a fix for the vulnerability is planned for the end of the year (2025)
2025-04-15: Receipt confirmed, and the issue was clarified once more, along with a recommendation for prompt resolution
2025-06-17: Public disclosure
As is normal for security researchers, without near-term fixes in place, the vulnerabilities were publicly disclosed on June 17th, 2025, shortly after the 90-day threshold expired. This includes the detailed reproduction steps, and code, to take advantage of each of these issues in the real world. Typically, researchers will withhold public disclosure if a manufacturer is working with them to get the fixes published in a timely manner.
While releasing these details might sound harsh to those outside the IT security world, the way COROS handled things up until yesterday was largely in line with a company that didn’t care. Saying that these massive security holes wouldn’t be fixed till the end of the year, in most security circles, would be considered jaw-dropping. After all, this wasn’t ‘just’ one minor security issue, or even one major one. It was 8 major ones that give attackers access to literally everything: The watch itself/operations, your watch data, and your COROS.com account. In addition to injecting false information sent to you, such as fake text notifications (or snooping on all of your text messages and/or notifications sent to the watch by your phone, which, for most people, is at a minimum, all text messages).
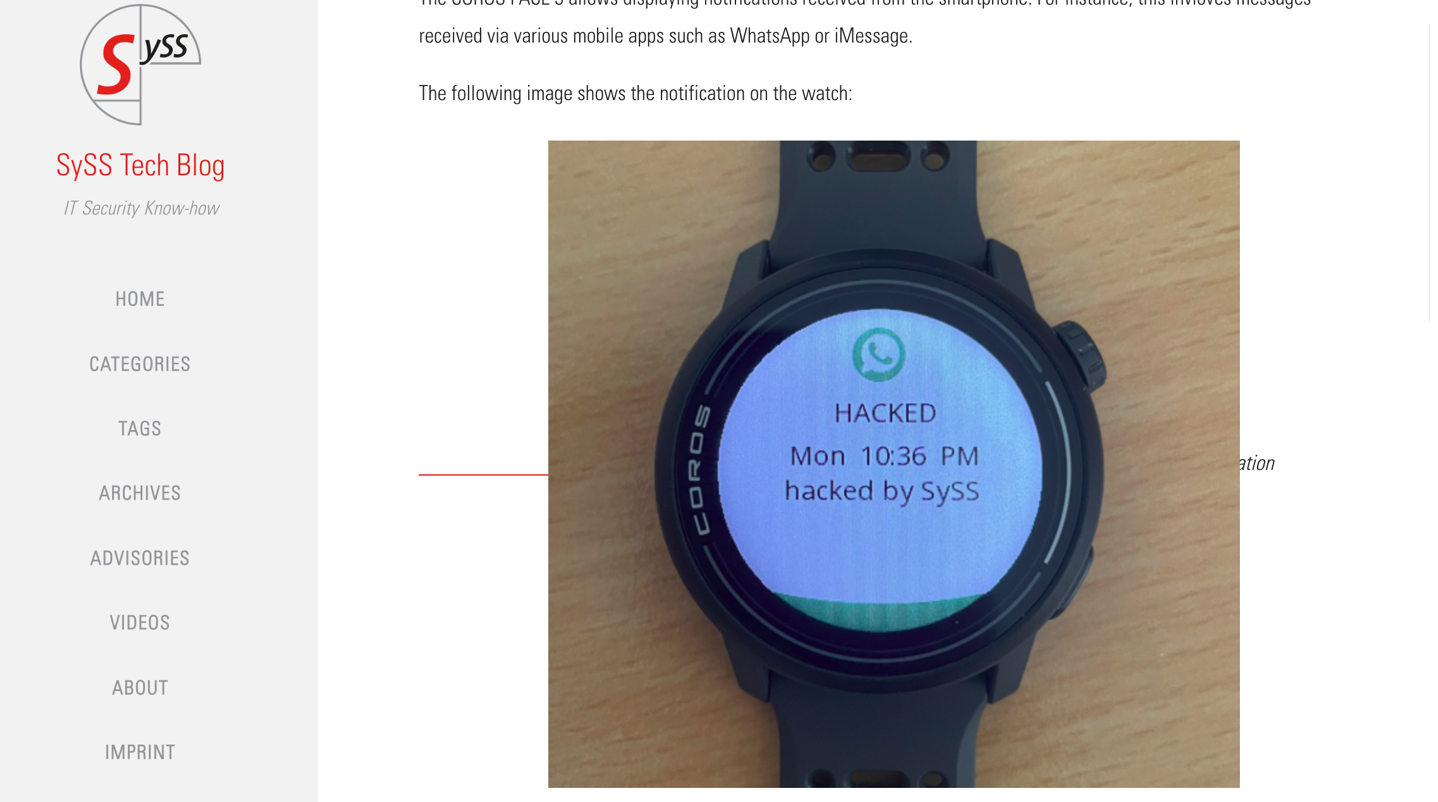
(Details from SySS, the IT Security research firm)
After a user sent me a link to the post on Friday night, I reached out to COROS to find out more. After all, this was an incredibly detailed list of issues, and it seemed like COROS mostly shrugged at them. For this e-mail, I went with the ‘cause a ruckus’ approach of including the CEO, their Head of Product Marketing & Support, their internal head of PR (Public Relations), and two more people from their external PR firm (one each in Europe and North America). In it, I had two simple questions:
1) Do these actually impact all COROS watches?
2) Why are these updates being pushed so far down the road?
Within a few hours (on a Friday night), I had received the first confirmation e-mail that they had received my note and were digging into it. Within 48 hours, I had received a long, detailed note from their CEO outlining the answers to my questions, as well as a bit more detail on how things fell apart on the COROS side.
First up, starting with the ‘which watches does this affect’ question, Lewis Wu, COROS’s CEO confirmed the following:
“The Bluetooth stack is largely shared across our watches, so these vulnerabilities apply broadly to most COROS devices. There may be minor implementation differences across models, but the underlying Bluetooth configuration is consistent. PACE 3 was the focus of the SySS report, but we are treating this as a platform-level issue and applying fixes across our product line accordingly.”
Which then gets to the next question: Why on earth are these issues not being addressed more promptly?
“You’re right that we were initially notified earlier this year (around 82 days ago). When we were notified, we started working on the issues but I have to admit the priority should have been higher. It’s a learning for COROS to prioritize security related problems. We had responded to the individual who reported these concerns with an over-simplified answer of “before the end of 2025″, but should have been more specific on the timeline with each item rather than speaking in broad terms and stated these will be fixed long before the end of this year.”
I’ll set aside the late-night mental math error on the number of days, which according to the published days should have been 107 days, but at least everything else admits something got dropped.
From there, he outlined all 8 issues, and the timelines for each. There was previously one issue which was slated for a June update, though given it’s the last day of June, I suspect that got slid into July. In turn, roughly half of the issues are now slated for a July update, and the other half in August. They are grouped into the following:
3.1, 3.2, 3.3, 4.1: By the end of July.
4.2, 4.3, 4.4, 4.5: They require deeper architectural changes and extensive validation across firmware variants. So our goal is to fix them by the end of August.
Those numbers above mean nothing to people outside COROS (or myself), and they clarified in a future update that the two groups are:
3.x List: Ones tied to the pairing of Bluetooth devices
4.x List: Ones tied to the encryption of communication to the device
He went on to say:
“In summary, we will establish a better authentication process before and during pairing COROS devices (3.1, 3.2, 3.3 and 4.1) before the end of July. The remaining issues (4.2, 4.3, 4.4, 4.5) are related to COROS Bluetooth communications during the product use, which requires a better encrypted communication. We will need to go through all the historical COROS devices and update them one by one. The end of August is an aggressive goal, but we will try our best.”
In addition, he noted:
“We want to thank you again for escalating the issues. And it’s important for COROS as a growing company to take learning from it – not only how to solve the reported problems but also how to streamline our internal procedures.”
Ultimately, at this point, users will simply need to wait for the fixes to be implemented. That said, having worked in IT and its security-related aspects as my day job before this, there’s almost always an inflection point in every company’s history where they start to take security issues seriously. Or more specifically, the reporting and management of them.
Meaning, every single software product ever created will eventually have a security bug. That’s largely the nature of software development. What matters is how a company handles that bug/issue. In this case, it seems like it was basically thrown into the larger pile of bugs to deal with, rather than being properly categorized as a security issue. Most software companies have very distinct channels for what happens when a security bug/vulnerability comes in. They typically have very specific e-mail addresses for researchers to contact, and they then have hyper-specific processes internally to ensure it gets proper visibility immediately. And further, they typically have hyper-specific processes on how to coordinate with the security researcher.
But all this usually only happens after a company screws up once. In this case, I’d guess this is the ‘once’ for COROS. As their CEO noted, they’re going to implement a host of things to ensure that future security issues are addressed efficiently (because again, all companies will have security issues eventually).
In any case, as a user, be sure that the next COROS firmware updates that come along in July and August are applied to your device, as they will definitely be important. I’m guessing COROS will probably also try and push users extra hard on this one too.
With that – thanks for reading!
FOUND THIS POST USEFUL? SUPPORT THE SITE!
Hopefully, you found this post useful. The website is really a labor of love, so please consider becoming a DC RAINMAKER Supporter. This gets you an ad-free experience, and access to our (mostly) bi-monthly behind-the-scenes video series of “Shed Talkin’”.
Support DCRainMaker - Shop on Amazon
Otherwise, perhaps consider using the below link if shopping on Amazon. As an Amazon Associate, I earn from qualifying purchases. It doesn’t cost you anything extra, but your purchases help support this website a lot. It could simply be buying toilet paper, or this pizza oven we use and love.




















As a COROS fan and a software developer…this is an embarrassing response to a zero day.
I use my sports watch for sports and I don’t care so much if some idiot steals my heart rate values.
It’s easy to dismiss privacy concerns with a thought like, “My heart rate data? So what?” However, these security flaws extend well beyond that. Imagine devices crashing at major events, or a malicious actor secretly accessing your messages and notifications. While sharing sports data might seem harmless, I believe most of us would be very concerned if our private messages were being monitored.
What other information is in your Coros account? Your emergency contact person’s details? Your email address and phone number? Where you live, from your activity profile? The fact that you’re away from home at present? What time you go for a run every morning? I could go on. The only saving grace here is that you need Bluetooth proximity to carry out this hack, but unless you plan on avoiding every bar, tram, bus, public park etc., you’re a sitting duck.
Additionally, this would include potentially a copy of all messages sent to your watch (via your phone). e.g. text messages, smartphone notifications, etc…
For most people, that’s likely the bigger security concern.
Garmin manages to reset millions of watches to factory settings without hacking. See the magic GPS triangle a few months ago
I follow you. Just the idea that someone knows things about you or is even tracking you without your knowledge is reason enough.
I don’t care about my heart rate, my pace, my power data, or my elevation gains. That stuff, as far as I’m concerned, can be public.
What I DO care about is my location data. Most notably, my home address (and, to a lesser extent, my work address.) Knowing that I’m a long distance triathlete, that my home address is this specific spot in this specific city, and that I’m generally out for an hour or more doing (swimming|cycling|running) at this specific time of the day – that’s gold for thieves.
This is a Big Bloody Deal, even if you don’t think it is.
Anecdata: one of my friends didn’t conceal his home region on Strava. Somebody – a complete stranger to him – swung by and asked him, “Are you ?” They’d tracked down his home from where he tended to start and stop his long rides. The implications are deeply, deeply profound, and they only get more serious the more you think about it.
(As a side note, I’m still annoyed that Garmin takes an “all or nothing” approach to data. I’m happy for them to gather and collate the cumulative load, sleep data, and similar; what I don’t want is all of my GPS data to go with it. But there’s no way to say “pass through GPS activities to TrainingPeaks [my coach has a definite need to know exactly what I’ve been doing], but don’t store it; everything else is fine to store and collate across my devices.”)
OK, but how about if your sports watch, which is connected to your phone, which is connected to your banking/government identification/personal email/password manager/etc gets hacked? Care then?
To be clear, it’s not clear to me that any of that can happen based on this disclosure. But how do we know there haven’t been other disclosures to Coros where that *is* a possibility? It’s not so much this vulnerability in particular, but rather Coros’ culture towards disclosed vulnerabilities as a whole.
@Stuart: That recent Wired article “Anyone Can Buy Data Tracking US Soldiers and Spies to Nuclear Vaults and Brothels in Germany” should be ringing major alarm bells for anyone wearing a smartwatch and connecting to apps with location services enabled. I’m with you, I don’t mind the data in motion across Garmin/Strava’s servers. It’s the data at rest afterwards that can be massively correlated that scares me.
One possible vector of attack: stalking
Second possible vector of attack: stealing all important data from Coros-sponsored professional athletes (imagine obtaining this data from someone like Pogacar or Vingegaard?)
Third possible vector of attack: stealing 2-auth codes from the messages you receive
It’s not just that data might be stolen. In certain countries (well, one mainly) it could very well end with some people being denied medical insurance. A bunch of health and personal data will identify you very specifically and could include enough evidence of preexisting conditions that insurance would become an issue.
This data is worth a lot more to legitimate businesses than it is on the “dark web”. In Europe it’s not an issue so much as GDPR would require an explanation as to where the data came from, but other countries have gone in the opposite direction so the data could easily be used without question.
COROS has released today the update tackling this matter.
“If the mobile phone or COROS app does not enforce pairing and bonding, the BLE communication on its physical layer is not encrypted and can be sniffed.”
That is crazy
I still remember what happened when a major brand was down for several days and to this day I’m still not sure how safe my data was or what really happened. Also was not informed of it. As a EU user, poor handling of the problem. It seems like the other brands don’t care either.
I believe that the “major brand” had a crypto locker malware attack and this encrypted the data on their servers. This revealed likely a lack of network segmentation or “physical” barriers between engineering or business users and the operational data center. Also the entire system is clearly based on Windows for servers which is not the architecture for a contemporary scalable highly resilient web service.
Is the data from Suunto, Garmin and Polar based in the EU you think?
Crees que el hecho de que Coros mantenga la obsesión de tener BT siempre activo, está relacionado con esto?
No entiendo por otro lado porque no escuchan a aquellas personas que no queremos dormir con el BT conectado. Nunca permitieron modo avión, y yo devolví mi Coros por esa “absurda” razon
I am shutting down my Coros Pace 2 immediately and not turning it back on until fixes are implemented, at which point I’m likely to sell it. It is a decent watch, but the company’s attitude is too reckless given how sensitive the data is.
I am in no way saying this is okay, but it does seem for a recreational runner that has never used notifications on a watch there is little concern out there. Especially if I do not do many races. Western States being this last weekend and having so so many Coros’ in the field that would have seemed to be the perfect time to do something if someone was going to do it.
The part I did not understand is does the bad actor have to be physically present to exploit the issue or can they be launched remotely?
I know we live in very interesing times, but I am not sure babys and bathwater are the answer. As previously stated, the response is pathetic and is about how their support works in the real world. It is really bad and very unresponsive to any concerns.
I think Ray says it best, this is a before and after moment.
It’s not so much the bugs themselves, but rather how the company handles them. It’s like calling your plumber to say a pipe has burst and your basement is flooding, and they reply: “I’ll definitely try to come by before the end of the year.” Also, did you received a message from Coros (if you have one)? I didn’t. It’s only by the work of Ray we know this.
Does this have cvss tracking or scores. Curious how this would rate on that scale
in this article following the link to SySS publication, at the bottom
Hey all, I wanted to comment here to add some additional information from the COROS side, and most importantly what we are doing to fix the issues reported and better manage similar reports like this in the future.
The vulnerabilities flagged were responsibly disclosed to us earlier this year as Ray noted, and we’ve been actively working on fixes since then (mid-March). We have a responsibility to our users to handle these issues with the utmost urgency and we acknowledge that we should have been quicker to fix these vulnerabilities from their discovery.
Some of the issues like improving how devices pair and authenticate, are already being patched this month and will be released in an update within the next couple few weeks with an app/firmware update when testing is complete. Others, which require deeper changes to how Bluetooth communication is encrypted during use, will be resolved by the end of August across all COROS devices.
While these issues documented in the report are difficult to exploit in the real world, we’re treating them seriously and rolling out updates as fast as we can without compromising performance or stability.
We appreciate the community holding us to a high standard, and we’re committed to learning from this, assigning a higher priority to all security vulnerabilities in the future, and we will do better in the future.
If your watch is up to date, there’s nothing you need to do immediately. When our next software updates are available in July and August, please be sure to update your watch which will fix the vulnerabilities mentioned. As always, if you have any questions, we’re here to help.
— Darian
Darian, I appreciate your willingness to try to scrape off some of the egg that is on Coros’s face. However, this is not a “high standard,” this goes back to bare minimum security responses. DCR is correct; most working in the security field would find the “fix two months from now” response AFTER the vulnerability is disclosed WILD in comparison to the response most companies have to serious vulnerability disclosures.
I’m not intimate with Coros’ inner workings to know how large the teams are, but it would seem that the opportunity to fix this PR issue was BEFORE the disclosure period ended, not a hastily back-pedaled response to the community after the vulnerability was disclosed responsibly and then nothing was done.
Totally reasonable to have security vulnerabilities – every company has one and if they don’t then they aren’t making interesting products. However, this response is garbage.
> While these issues documented in the report are difficult to exploit in the real world
I would like to point out the security researcher blog post literally contains source code to get an Android phone with COROS app installed to leak the COROS account API key and example code for other attack vectors too. Somebody surely must have Android somewhere, even as a test device? Right?
Well, sorry, but it is not as if we were in the 90s and exploitation of online security deficits was almost unheard of. Coros runs a multi million dollar business that involves people‘s personal data. Mistakes happen nevertheless but you have to manage them accordingly. I am quite happy, that I don’t have the Coros problem myself. And probably never will.
That’s the way Lewis works. Half ass ideas and then backtrack when it bites him in the ass. Then Darian is left to clean up the mess (and that’s not a compliment).
This comment feels like such an empty response. A properly functioning engineering team would provide a way or instructions for users to protect themselves from these exploits even if that might be a detriment to the UX (can I just turn off Bluetooth?).
Additionally, with how poorly this has gone a public post mortem would be a very reasonable expectation from users. How is Coros going to prevent issues like this? Even after this was prioritized why is the fix taking so long? Is the engineering team properly resourced to support such a large user base? Is there a security team at Coros? Who is the engineering and security leadership? Was this security researcher compensated? There are so many questions unanswered and for a vulnerability like this transparency is very important
At least Polar should be, as that is a finnish company and should adhere to EU Law. I’m REALLY glad that Cyber Resilience Act is coming to catch sloppy programmers and hold them accountable for lack of using the brain.
Good job Ray.
My personal moment was ShellShock, and having millions of vulnerable devices in people’s homes.
We patched the issue within 3 days and rolled out new firmware with a streamlined release process.
After that, security had a higher profile, and subsequent vulnerabilities got more attention and fixed faster.
Super, super disappointed. I was ready to jump from the increasingly overpriced, wackadoodle cost of Garmin to Coros. I’ve been on Garmin since a FR 305! But the laissez-faire response from Coros? They are dead to me. Really, these obvious vulnerabilities should never have exposed consumers in the first place. Blatant disregard for security = no interest from me.
This absence of basic wire encryption stuff is truly embarrassing amateur hour.
The fuzzing crashing the device… well I am fairly confident that Garmin OS for the fenix 8 could not survive that either.
They have most definitely messed up more than once.
This isn’t their first vulnerability link to zhouhanc.com
Seeing this I was curious what the engineering org at Coros looked like (and if they were hiring to expedite these fixes) and noticed a severe lack of information. I couldn’t find many software engineers working at Coros nor any signs of engineering leadership on LinkedIn or otherwise.
I kind of assumed that most of these wearable companies were structured similarly to Whoop which has a large engineering organization but it seems that assumption is wrong. Definitely something I need to pay more attention to when I purchase technology. Certainly a well functioning engineering org with strong leadership would have identified the severity and urgency of this issue and would have expedited the fixes at the very least. As a software engineer I understand the complexity of a fix like this but at the same time it feels like they are not investing enough into the engineering function at Coros and I will definitely consider switching to a more engineering focused company for my wearables in the future.
All their engineers are based in China. I’m not sure that’s even very trustworthy.
Products from Chinese IT companies have always been suspected of security issues. They have been suspected of intentionally leaking users’ information, not by mistake. To be honest, pure Chinese companies cannot be trusted. They are under the strong control of the Chinese government.
So Polar and Garmin are the only ones left?
We must not forget that Huawei products from China were sold in the United States with hidden backdoors.
don’t be overconfident in any countries, particularly USA ;-)
link to spyscape.com
Long time Garmin user here. I bought a COROS PACE 3 earlier this year because of price and battery life, but after reading this original story from DC Rainmaker, I immediately stopped using my COROS watch. I cannot even give it away to anyone and it’s essentially brand new. The trust is gone with me and COROS and I wonder how many others will go back to Garmin after this?
I’d like to see the results of the software audit conducted by an external company. Is COROS planning to carry out such an audit?
Garmin did it, but they weren’t WhiteHat guys :-)
link to bleepingcomputer.com
From what I’ve read it’s not possible to turn off BT on Coros? If that’s true, then introducing that feature could have been a short-term patch, at least for some situations.
No expert on this but maybe, keeping the Bluetooth on saves batterij instead of always the need to search for a connection. Maybe that is what they focus on to get good battery results
seems like there was an update of the coros app yesterday (at least on ios) to address this issue
I’ll try and get some clarity on which specific security issues have been addressed in the latest update, and which ones are still on the table.
They have a page covering some of the basics: link to support.coros.com
But unfortunately, it doesn’t simply list out the CVE’s to make it easier (most companies would specify a CVE or other internal/company tracking number to security updates).
Did you get any clarity on updates for the security issues?